What Are Program Invisible Registers
Warm-up Questions

Keypoint :
Address - Location of Data
Information - What exactly stored in address
Reference Bespeak = 1st byte of the sequence
Logical address = relative distance from 1st byte
Logical address permit user to ignore retentivity (relocatable)
Concrete accost = Address
Little Endian and Big Endian
Most Significant Byte = Leftmost Byte in 0x
Least Significant Byte = Rightmost Byte in 0x
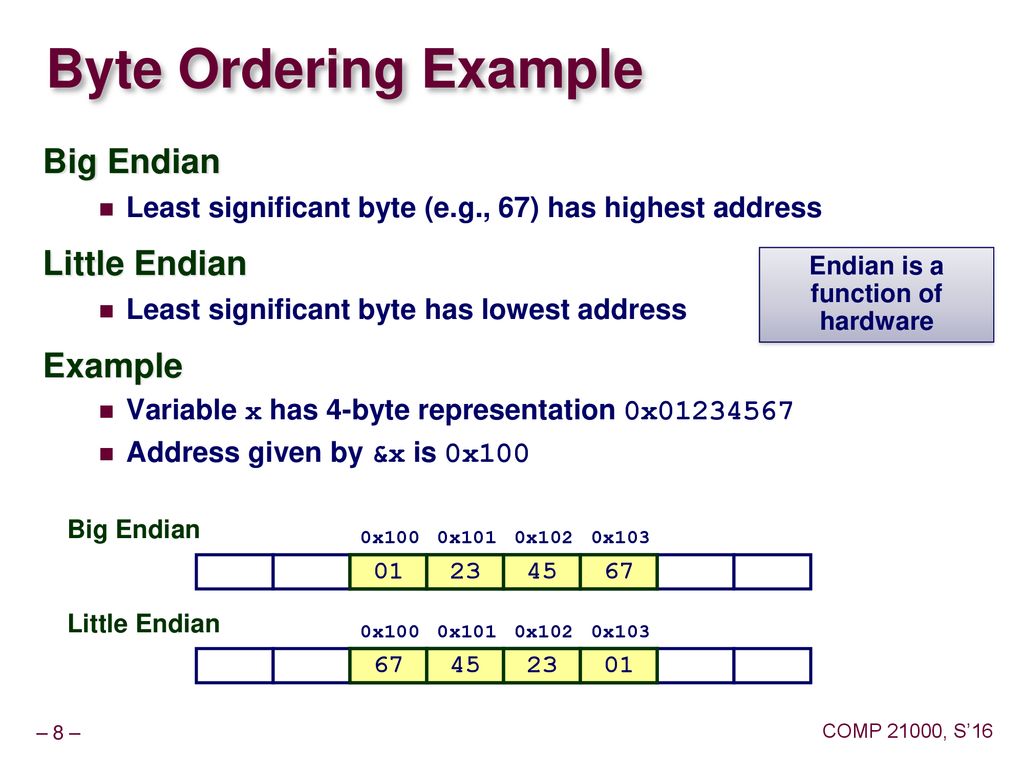
Eastward.g. Data is 1234H, Because 12|34 , MSB = 12H, LSB = 34H
At present we have Address : 1000H and 1001H
In Little Endian format, LSB has lowest address.
12H -> 1001H
34H -> 1000H
Life cycle of Logical Address and Concrete Accost:
- Logical Address (Car Lawmaking Exist)- A Relative Sequence. Elimated once the file/disk/division is deleted.
- Have Machine Lawmaking = Logical Address
- Concrete Address (In estimator) - Different everytime when you run a program. Elimated once the program is ended, Curt life bike
- Plan's Hard disk drive (Secondary Memory) -> Memory'due south Card's RAM (Primary Memory) = Have Physical Address
(a) Logical address at 5002H = 2
(b) Physical accost at 5003H = 5003H
© Logical address of 5th byte = 4
(d) Physical address of 5th byte = 5004H
(east) N.A.
Note: If program is not beingness loaded into computer memory, in that location will be no physical address.
The answer is Nil/ Dont Know.
(f)
Information A is composed of 2 bytes. We utilise footling endian format here, Higher address has higher significant byte. 42H is LSB, 11H is MSB
Therefore Value of Data A : 11|42 -> 1142H
If nosotros use Big endian format, the value of Data A will be 4211H.
(g)
Logical accost volition ever have longing life cycle than physical address.
(h)
Provide address of least pregnant byte -> Lowest accost -> 42H -> 5006H
Yes. 5006H is physical accost.

Char/Int = ane byte = 8 scrap
Word = two byte = sixteen scrap
Doubleword = four byte = 32 bit
Quadword = 8 byte = 64 bit
:: = 2^north byte
Keypoints:
Signed = with sign flake
Unsigned = without sign fleck (must exist positive)
1'south complement: invert each bit of a number from 0 to one or from 1 to 0.
(a),(b),©,(d):

(e)
In theory, yous can, but you won't do it in practice. A computer is designed in a fashion that the starting address of a byte/discussion/doubleword/quadword must exist integer multiples of i/2/4/8 so every bit to reduce the hardware complexity. If y'all follow the rule, you lot can fetch the requested information in one single data transfer. When compiling your programme, the complier automatically handles this for your program to produce motorcar codes under the dominion.

Composition of a Computer System
Microprocessor is a core component of a figurer arrangement.
More powerful microprocessor => more than powerful computer arrangement particularly when it works with other matched system components.

CPU
a general-purpose processor that executes all instructions and controls all information move in the computer organization.
Central Processing Unit of measurement (CPU) contains
- Arithmetics logic unit (ALU) - contains electrical circuits that deport out each educational activity
- Registers - shop data or instructions that are needed immediately or frequently.
- Control unit (CU)
- Command movement of data to and from CPU registers and other hardware components.
- Access plan instructions and issue appropriate commands to the ALU.
System motorbus
A bus is a shared electrical or optical channel that connect ii or more devices.
A system autobus is the master channel for moving data and instructions to and from hardware components.
Its capacity is a disquisitional cistron in reckoner performance.
Two busses with different capacities (bandwidths) tin can exist continued if we place a controller (chosen a bridge) between them.
A coach tin can as well exist classified based on the nature of the information that information technology transfers betwixt the microprocessor and its memory and I/O devices:
- Address bus - transfer address information
- Information omnibus - transfer data data
- Control jitney - transfer control data
Wider width => higher data transfer rate (Data Bus) / back up larger memory space (Accost Bus)
Master Storage
Also referred to as master memory, or merely memory.
Contains millions or billions of storage locations that hold
- currently executing program instructions
- data being processed by these instructions
is implemented with silicon-based semiconductor devices (Mainly RAM)
Secondary Storage
Secondary Storage is composed of high-chapters nonvolatile storage devices that concur the following:
- Programs not currently runnin
- Data not needed by currently running programs
- Data needed by currently running programs that doesn't fit in available primary storage (Virtual retentiveness)
is constructed with slower and less expensive technology to proceed full cost inside acceptable limits.
I/O devices
The diverseness of I/O devices in modern computers addresses the many different forms of human-to-computer and estimator-to-computer advice.
I/O devices tin exist classified broadly into human-oriented and calculator- oriented communication devices.
Management of the memory & I/O systems

Each memory location is associated with a memory address.
A CPU accesses a retentivity location with the address bus.
The width of the address autobus (in terms of bits) defines how many retention locations that a CPU tin access theoretically.
Each port is associated with a port address.
A CPU accesses a port with the address charabanc.

The microprocessor and its architecture
Internal microprocessor architecture
Earlier a program is written or whatsoever didactics is investigated, the internal configuration of the microprocessor must be known.

Due south stands for Segment
Nomenclature of registers:
- Visible/invisible
- General purpose/special purpose
Plan visible/invisible
Program visible registers:
- are used during programming and specified past the instructions.
- Segment registers are visible registers.
Programme invisible registers:
-
tin not exist addressable directly during applications programming but may be used indirectly during system programming are considered.
- Descriptor cache, descriptor tabular array addresses are invisible registers.
General/Special-purpose
Some registers are full general-purpose or multipurpose registers, while some have special purposes.
Multi-purpose registers:
- hold various information sizes (bytes, words, or doublewords)
- are used for almost whatsoever purpose as dictated by a plan
- Just sometimes are used for some special purposes.
BP stand for base arrow
DI correspond Destination Index
SI stand for Source Index
Example:
| Annals | Usage |
|---|---|
| EAX/AX | dedicated for instructions such as multiplication, division, and some of the aligning instuctions |
| EBX/BX | sometimes holds the starting time accost of a location in the retentiveness organisation. |
| ECX/CX | also used to holds the count for various instructions. |
| EDX/DX | holds a part of the result from a multiplication or part of the dividend before a partitioning. |
| EBP/BP | points to a memory location for memory information transfer (pointer). |
| EDI/DI | ofttimes addresses destination cord data for the string instructions. |
| ESI/SI | often addresses source string data for the string instructions. |
Special-purpose registers
These registers are used for special purpose.
Example:
| Register | Usage |
|---|---|
| EIP/IP | addresses the next education in a department of memory defined as a lawmaking segment. |
| ESP/SP | addresses the tiptop of the stack. |
| EFLAGS/FLAGS | betoken the condition of the microprocessor besides every bit command its operation. |
| CS | defines the area of retentiveness used to concord the code. (generate memory addresses when combined with other registers in the microprocessor.) |
| DS | defines the surface area of retentiveness used to hold the information used past a program. (generate memory addresses when combined with other registers in the microprocessor.) |
| ES | defines the surface area of memory used past some of the cord instructions to concur destination data. (generate retentivity addresses when combined with other registers in the microprocessor.) |
| SS | defines the area of retentivity used for the stack (generate memory addresses when combined with other registers in the microprocessor.) |
| FS/GS | supplemental segment registers bachelor in the 80386 and in a higher place microprocessors to allow ii additional memory segments for access by programs.(generate memory addresses when combined with other registers in the microprocessor.) |
Existent mode memory addressing
In real mode operation, information technology allows an Intel CPU to address merely the offset 1M byte of retention space (even the Pentium microprocessor).
Existent mode operation
- Allows downward compatibility
- Is the default performance mode
- begins operation in the real mode by default whenever power is applied or the microprocessor is reset.
- allows application software written for the 8088/8086, which contain merely 1M byte of memory, to part in the 80286 and above without changing the software.
The commencement 1M byte of retentiveness is called either the real memory or conventional memory system.
Segments and offsets
A combination of a segment address and an offset address access a memory location in the real mode.
The segment address, located within one of the segment registers, defines the beginning accost of whatsoever 64K-byte memory segment.
The beginning accost selects any location within the 64K-byte memory segment.
Size of a segment = 64K bytes


A 20-bit real mode address allows one to admission the start of a segment at any 16-byte boundary within the first 1M byte of retention (address 00000- FFFFFH).
Any real mode segments can only begin at a 16-byte boundary in the memory system and this purlieus is often called a paragraph.
Size of a paragraph = 16 bytes
The starting address of any paragraph is a multiple of sixteen.
Default segment and offset registers
The microprocessors has a set of rules that employ to segments whenever memory is addressed.
These rules, which apply in either the existent or protected fashion, define the segment register and offset annals combination used past certain addressing modes.

CS - code segment annals
- defines the beginning of the code segment
IP - educational activity pointer
- locates the adjacent instruction within the lawmaking segment
Stack data are references through the stack segment at the memory location addressed by either the stack pointer (SP) or the base pointer (BP).
A program can have a lot of segments, but can simply access at most 4 (in 8086-80286) or 6 (in 80386 and above) segments at a fourth dimension.
Note: Segments can overlap with each other.
Relocation
Segment and offset addressing scheme allows relocation.
- A relocatable plan is 1 that can be:
- placed into any surface area of memory
- executed without change.
- Relocatable data are data that can be:
- placed in any area of memory
- used without whatsoever modify to the plan.

Memory is addressed within a segment by an offset address.
the memory segment can exist moved to any place in the memory organization without irresolute any of the offset address by moving the unabridged program, as a cake, to a new expanse and so changing simply the contents of the segment registers.
Protected mode retentivity addressing
Protected mode retentiveness addressing(80286 and in a higher place) allows admission to data and programs located above the get-go 1M byte of retentivity likewise equally inside the first 1M byte of retentiveness.
Tin admission more than than 1M byte
In Protected Way:
- Segment register is interpreted differently in different modes by the microprocessor to admission the retention segment.
- Segment register contains a selector that selects a descriptor from a descriptor table instead of a segment address.
- descriptor describes the memory segment's location, length, and admission rights.
Selectors
The selector, located in the segment register, selects i of 8192 descriptors from one of two tables of descriptors.

The segment annals contains:
- a 13-bit selector field
- a table selector (TI) bit
- a requested privilege level field
The TI bit selects either the global descriptor table (TI=0) or the local descriptor tabular array.(TI=ane).
TI = 0 => GDT
TI = one => LDT
The requested privilege level (RPL) requests the access privilege level of a retentivity segment.
- The highest level is 00 and the everyman is 11.
Descriptors
describes the memory segment's location, length, and access rights of the segment of memory.
There are 2 descriptor tables.
- global descriptors contain segment definitions that employ to all programs.
- local descriptors are usually unique to an application.
Each descriptor table contains 8192 descriptors.
Each descriptor is viii bytes in length.
The base address portion of the descriptor indicates the starting location of the memory segment.
base accost = starting location of the memory segment
The paragraph purlieus limitation is removed in protected mode.
The segment limit contains the last starting time address constitute in a segment.
E.thousand. if a segment begins at memory location F00000H and ends at location F000FFH,
- the base address = F00000H
- the limit = FFH.
Descriptor 0 is called the naught descriptor and may not be used for accessing retentivity.
Improve the performance with program-invisible registers
- The global and local descriptor tables are placed in the retentivity system.
- 80286 and above contain programme-invisible registers to access and specify the accost of these tables.
- The plan invisible registers are not directly addressed past software.
- These registers control the microprocessor when operated in the protected mode.



- Each of the segment registers contains a plan-invisible portion used in the protected way.
- The program-invisible portion of the segment register is loaded with the base address, limit, and access rights each time the number in the segment annals is changed.
- This allows the microprocessor to access a retentivity segment repeatedly without referring back to the descriptor table for each access.
- The GDTR (global descriptor tabular array register) and IDTR (interrupt descriptor table annals) contain the base of operations address of the descriptor tabular array and its limit.
- When protected mode performance is desired, the address of the global descriptor tabular array and its limit are loaded into the GDTR.
- Before using protected style, the interrupt descriptor table and the IDTR must be initialized.
- The location of the local descriptor tabular array is selected from the global descriptor table.
- One of the global descriptors is gear up to address the local descriptor tabular array.
- To access the local descriptor table, the LDTR is loaded with a selector, merely as a segment register is loaded with a selector.
- The job register holds a selector that accesses a descriptor that defines a task.
- Chore switching allows multitasking systems to switch from one task to another in a elementary and orderly way.
Real fashion vs Protected way
In that location are 2 way operation.
Real Mode:
- No Multi-tasking
- could address simply the beginning 1M byte of retention space
- All processor have real mode bachelor.
- Used past DOS and Standard DOS applications.
Protected fashion is a much more powerful mode of operation than real fashion, and is used in all modernistic multitasking operating systems (Bone).
Protected Mode:
- Support Multi-tasking
- Full admission to all of the arrangement's retention (no 1M limit)
- Back up for virtual memory
- Faster (32-flake) access to retentivity and faster 32-bits drivers to do I/O transfers
- All of the major Bone today use protected fashion, including Windows, Linux.
- If a program tries to use a memory accost that information technology isn't allowed to, a "protection fault" is generated.
| Existent Mode | Protected Mode | |
|---|---|---|
| Detect Segment Size | 64k byte | Limit + Starting Address |
| Discover Starting Address | Segment annals x sixteen (i.due east. 10H) | Segment register with Descriptor |
Memory paging
Paging performs logical to physical address translation.
Paging allows any program and data relocatable (Even more powerful than the segment and commencement addressing scheme.).
How paging works in Intel's CPU:
- The memory space is divided into a number of pages.
- Each folio is of size 4 Kbytes.
- Any data/program is divided into pages of size 4 Kbytes each and these pages are individually loaded into the memory space.
- Any information/program byte is associated with a logical address.
- The dir:page info tells which page the requested data is in.
- The showtime tells which byte in the specified page is the requested data

Paging registers
The paging unit is controlled by the contents of the microprocessor's control registers.
A page of memory = 4K bytes of retentivity.

The page directory and page tabular array
- A folio directory contains entries that locate the starting addresses of up to 1024 page tables.
- Each page table contains 1024 entries that locate the starting addresses of 1024 pages.
A page table = 1024 pages
=> 1024 4K = 4M memory.
A page directory = 1024 folio tables = 1024 1024 pages
=> 1024 1024 4K = 4G memory.
Paging vs No Paging:
Access three Times vs Access Once

Retentiveness Paging - Detailed Explanation


Storage overhead
Basically:
The page directory plus the page tables could be a big storage overhead to the retention system.
E.one thousand. A paged memory arrangement of 4G bytes must allocate 4K bytes of retentivity for the page directory and 4Kx1024 bytes for the 1024 page tables.
Time overhead
- Repaging a 4K byte section of memory requires access to the page directory and a page table, both located in retentiveness.
Time overhead: Solution
Intel has incorporated a cache called TLB (translation look-aside buffer) to agree the nigh recent page translation addresses to speed up the translation.
Exercises

(a) True. Any real mode segments tin can only begin at a 16-byte purlieus in the memory arrangement and this boundary is often called a paragraph.
(b) Fake. In real mode, physical accost is provided instead of logical address.
© True. Merely to the lowest degree significant 16 bits of EAX (Extended AX) volition be used in real fashion functioning as AX register.
(d) True. In 8086-Organisation, Tin can handle at most iv active segments.
(due east) False. Segments tin can overlap with each other.
(f) False. IP (Instruction Arrow) is not related to segment instead, it is related to get-go. IP locates the next instruction inside the code segment.
(g) False. It is 1FFH instead of 1000H
Seg: 100H
Offest: FFH
Accost: 1FFH
(h) True. A Segment annals is used to define the starting accost of a segment.
(i) True. An offset register is used to specify the deportation of a datum from the starting address of the segment in which the datum is.
(j) Imitation. It is determined past the size of the offset annals instead of the offset register.
(k) Truthful. relocatable.
(l) False. Information technology is not e'er case as you can use other combination.
(one thousand) True. Paragraph is a multiple of sixteen.

Keypoint:
A page of memory = 4K bytes of retention
A page table = 1024 pages
=> 1024 4K = 4M memory.
A page directory = 1024 page tables = 1024 1024 pages
=> 1024 1024 4K = 4G memory.
(a)
No. of memory page in main memory = 2G bytes/4K bytes = 0.5M pages
one Folio table entry (PTE) for 1 memory page -> 0.5M PTEs for 0.5M memory pages
Retentiveness for storing pages tables = 0.5M PTEs x 4 bytes/PTE = 2M bytes
1 page tabular array handles 1K PTEs -> No. of page tables = 0.5M PTEs/1K PTEs = 0.5K page tables
1 folio directory entry (PDE) for i folio tabular array -> 0.5K PDEs for 0.5K page tables -> ane page directory (tin can handle 1K PDEs) is required.
Total storage overhead: 1 folio (4K bytes) for folio directory + 512 pages (2M bytes) for page tables (~0.1 Memory)
(b)
Time overhead: An address translation has to exist washed whenever in that location is a information transfer.
3 Memory access are required to access a data. In contrast, only 1 memory access is required to fetch a information when paging is not used.
Time overhead = the actress amount required to access memory location when the paging system is on.
Solution: Intel uses a cache chosen TLB (translation look-aside buffer) to concur the nearly recent page translation address to speed up the translation.

| In an 80386 Arrangement | Real Fashion | Protected Fashion |
|---|---|---|
| Size of a segment | 64K, fixed | Variable (= limit + 1 <= ii^xx in 80386) |
| Base address of a segment | must be a multiple of 16 | Can be anywhere in the chief memory |
| Content of segment register | After multiplied by xvi, it shows the starting bespeak of a segment | It is a pointer to a descriptor |

GDT = Global Descriptor Table. starting accost of GDT is adamant past GDTR
LDT = Local Descriptor Table. starting address of LDT is determined by LDTR and CS
GDTR = Global Descriptor Register (Base of operations Address)
LDTR = Local Descriptor Annals.

(a) 1A0000H. Since the base of operations address fleid of GDTR is 1A0000H.
(b) Note : Descriptor one = , Descriptor 2 =

Therefore Descriptor 16 = =
Address of Virtually significant byte = =
© 112244H. starting address of LDT is adamant by LDTR.
Change LDTR into xvi bit Binary: 10H = 0000 0000 0001 0 0 00B
First 13 flake is Selector, then one bit TI, 2bit RPL(requested privilege level).

Now you know that Selector = ii. (Binary Value of 10 = 2)
TI = 0 => GDT. Nosotros Select descriptor ii of GDT.

FROM Descriptor 2, nosotros have 0000,XX11,2244,1FFFH.
base address (S.A.) of LDT = 112244H, Limit of LDT= 1FFFH, Size of LDT = 2000H (i.eastward. 8912).
Ending Address (Due east.A.) of LDT = S.A. + Limit = 112244H + 1FFFH = 114243H.
(d) From ©, base of operations address of LDT = 112244H, limit of LDT = 1FFFH, Admission correct of LDT = 20 (i.e. don't care)

(eastward) For GDTR, Nosotros don't know the limit. Therefore, we assume that GDT is fully occupied by 8192 Descriptors.
At present we can estimate the GDT size = 8192 eight bytes = 64K bytes = 10000H bytes
Starting Accost of GDT = 1A0000H (Given)
Ending Accost of GDT = 1A0000H +10000H – 1 = 1AFFFFH
(f) Note: The size of a descriptor is 8.
Size of the LDT = 2000H (i.e. 8192) ⇒ No. of descriptors = 8192/8 = 1024 = 400H

(a)(i) Interpret the following logical addresses to physical addreses: 000C8090H
Firstly, Expend it into binary form:

000C8090H ⇒ 00,0000,0000 | 00,1100,yard | 0000,1001,0000 -> 0-C8H-90H
0 is the Entry of Page directory, C8H is the Entry of Page Table, 90H is the offset.
In this case, the Starting Address (S.A.) of the Page Directory is 00002000H.
Entry 0 in the Page directory = 00002000H + 0 4 = 00002000H
Now yous know Accost of entry 0 of the PD is 00002000H. Its content is 00003003H. (refer to figure)
Note : The size of a page must be 4k byte. This implies that the last 3 digit must be 000.
Even we have 00003003H, It is really 00003000H Since It must be an integer multiple of 4k.
Now Nosotros know the S.A. of Wanted Folio Tabular array is 00003000H.
Since S.A. of Wanted Page Table = 00003000H
Entry C8H of the Page Table = 00003000H + C8H 4 = 00003320H. Its content is 00110003H (refer to figure)
Since South.A. of the Target page is 00110000H.
The address of the 90Hth byte of the page = 00110000H + 90H = 00110090H
Logical address 000C8090H is mapped to physical address 00110090H.
Therefore the Physical address is 00110090H.
(a)(ii) Translate the following logical addresses to physical addreses: 00001000H
Firstly, Expend it into binary grade:

00001000H => 00,0000,0000 | 00,0000,0001 | 0000,0000,0000 -> 0-1H-0H
Entry of Page Directory: 0
Entry of Page Table: 1H
Outset: 0H
S.A. of Page Directory: 00002000H
Entry 0 of Folio Directory:
S.A. = 00002000H + 0 4 = 00002000H.
Content = 00003 003H (refer to figure)
Due south.A. of Page Table: 00003000H
Entry 1 of Page Table:
Due south.A. = 00003000H + 1H 4 = 00003004H
Content = 00001003 (refer to figure)
South.A. of Target Page = 00001000H
Outset = 0H
The address of the 900Hth byte of the page 00001000H + 0H = 00001000H
Therefore the Concrete address is 00001000H.
(a)(iii) Interpret the following logical addresses to concrete addreses: 000CA900H
Firstly, Expend it into binary form:

000CA900H => 00,0000,0000 | 00,1100,1010 | 1001,0000,0000 -> 0-CAH-900H
Entry of Page Directory: 0
Entry of Page Table: CAH
Commencement: 900H
S.A. of Page Directory: 00002000H
Entry 0 of Folio Directory:
S.A. = 00002000H + 0 4 = 00002000H.
Content = 00003 003H (refer to figure)
S.A. of Page Table: 00003000H
Entry CA of Page Table:
South.A. = 00003000H + CAH iv = 00003328H
Content = 00112003 (refer to figure)
Southward.A. of Target Page = 00112000H
Commencement = 900H
The address of the 900Hth byte of the page 00112000H + 900H = 00112900H.
Therefore the Physical address is 00112900H.

(b) What is the physical address of logical accost 00401001H if the content of address location 00002004H is 00002003H? What is its content in byte?
Firstly, Expend 00401001H into binary course:

00401001H => 00,0000,0001 | 00,0000,0001 | 0000,0000,0001 -> 1-1H-1H
This is Tricky.
Entry of Page Directory: 1
Entry of Page Table: 1H
Commencement: 1H
S.A. of Page Directory: 00002000H
Entry i of Page Directory:
Southward.A. = 00002000H + 1 4 = 00002004H.
Content = 00002003H (refer to question: the content of address location 00002004H is 00002003H)
S.A. of Page Table: 00002000H
Entry i of Page Table:
S.A. = 00002000H + 1H 4 = 00002004H
Content = 00002003H (refer to question: the content of accost location 00002004H is 00002003H)
Your wanted Page Table overlap with your page directory. It is possible.
Due south.A. of Target Page = 00002000H
Showtime = 1H
The address of the 900Hth byte of the page 00002000H + 1H = 00002001H.
Therefore the physical address is 00002001H.
To go Content in byte of 00002001H:
In 00002003H to 00002000H, the Content is 00 | 00 | xxx | 03 . (Doubleword)
03 => 00002000H
30 => 00002001H
00 => 00002002H
00 => 00002003H
Therefore 30H is the content of 00002001H.

© Suppose now the base of operations address of the folio directory is 3000H instead of 2000H. What is the concrete address of logical address 00800004H? What is its content in word?
Firstly, Expend 00800004H into binary form:

00800004H => 00,0000,0010 | 00,0000,0000 | 0000,0000,0100 -> 2-0H-4H
Entry of Page Directory: 2
Entry of Page Tabular array: 0H
Offset: 4H
S.A. of Page Directory: 00003000H
Entry 2 of Page Directory:
S.A. = 00003000H + 2 four = 00003008H.
Content = 00002003H (refer to graph)
S.A. of Folio Table: 00002000H
Entry 1 of Page Table:
S.A. = 00002000H + 0H 4 = 00002000H
Content = 00003003H (refer to graph)
S.A. of Target Folio = 00003000H
Commencement = 4H
The address of the 4Hth byte of the page 00003000H + 4H = 00003004H.
Therefore the physical address is 00003004H.
To get Content in give-and-take of 00003004H:
In 00003007H to 00003004H, the Content is 00 | 00 | 10 | 03 . (Doubleword)
03 => 00003004H
x => 00003005H
00 => 00003006H
00 => 00003007H
Equally they require Word, it is 2 byte.
Little endian -> High significant byte has higher address.
Therefore the Content = 1003H
Instructions and addressing modes
Basic Computer Functioning Wheel
A program is a sequence of instructions supported by the ISA of a microprocessor.
Instructions are fetched from the memory and executed 1 by 1.
Types of Instructions
- Processor-memory - transfer data betwixt processor and retentiveness
- Processor-I/O - data transferred to or from a peripheral device
- Information processing - arithmetic or logic operation on information
- Control - alter sequence of execution
What is a instruction cycle?
- the time period spent for executing an instruction
- The verbal fourth dimension duration varies from instruction to instruction

Basically :
- Fetch the instruction from retentiveness into a command register
- Decode the instruction
- Locate the operands used by the instruction
- Fetch operands from retention (if necessary)
- Execute the operation in processor register
- Shop the results in the proper place
- Go back to step one to fetch the next instruction

Assembly language
Machine language
How to program a CPU?
Machine language (machine lawmaking) is a sequence of flake patterns that a CPU can recognize and operate accordingly
A bit pattern will activate pre-defined action of digital circuit within the CPU chip and eventually perform a pre- defined functioning
Property of Machine language
- machine dependent
- difficult for humans to remember bit patterns simply meaningful names, so nosotros utilise names to denote patterns. (Each corresponds to an opcode.)
- Different combinations of opcode & operands form different instructions
- Each model of CPU has its own teaching set
- Education fix defines the operation, clock required, addressing modes supported, max. no. of operands associated with an opcode
Associates language
Assembly language is a depression level language, which means it is machine dependent.
High level language such as C/C++ and coffee is motorcar independent
An assembly language programme is actually a sequence of instructions.
Property of Assembly linguistic communication
An assembly language program typically has 4 fields:
- label
- opcode
- operand
- comment
Addressing modes tells how we can make up one's mind the exact location of the data (operand) nosotros desire to manipulate
Humans use assembly linguistic communication to write programs and use assembler to interpret associates programs into auto codes.
"Debug " is an environs for one to acquire and debug 8086 assembly language programs.
The MOV Teaching
More Info
MOV education that is used for moving data from ane storage space to another.
The MOV instruction takes ii operands.
Look at Addressing Modes.
Addressing Modes
Teaching Basics
An didactics in computer contains Opcode and Operand.
(Operand is optional)
Opcode - Specifies the operation to be performed
Operand - Specifies the data to bbe processed
Addressing modes
Addressing mode tells how nosotros tin determine the exact location of the data (operand) we want to manipulate
Operands are required for some operations (e.g. Add together)
The more powerful a CPU, the more modes it supports
Common Addressing modes
With Addressing Modes, we can detect the beginning.
- Implied Mode
- Firsthand Mode
- Register and Annals-Indirect Modes
- Direct Addressing Mode
- Indirect Addressing Way
- Relative Addressing Manner
- Indexed Addressing Mode
We use Intel's 8086 (real mode) as examples to study addressing modes

To get the real address:
Constructive accost = segment address x 16 + get-go address
Note: 10H = sixteen in binary.
KeyNote - Length of General Registers:
- 32 bits: EAX, EBX, ECX,EDX
- 16 bits: AX, BX, CX, DX
- 8 bits: AH, AL, BH, BL, CH, CL, DH, DL
i byte = 00H, 2 byte = 0000H, 4 byte = 00000000H
Go back to "Internal microprocessor architecture" if you forgot everything.
annals Style
Example:
Issue: content of AX change to the content of BX.

firsthand Fashion
Example:
Result: content of AX become 1B67.

direct style
Example:
Result: content of AX get the content of Address location 1B67.

register indirect fashion
Case:
Upshot: content of AX become the content of Address location BX.

base-plus-index manner
Example:
Effect: content of AX become the content of Address location BX+SI.

register relative style
Example:
Outcome: content of AX become the content of Accost location BX-three.

base relative-plus-alphabetize manner
Example:
Consequence: content of AX go the content of Address location BX+SI-ii.

Stack Memory
The stack memory is maintained past the stack pointer (SP) and the stack segment register (SS) in Intel's 8086.
The stack memory tin:
- holds data temporarily
- stores return addresses for procedures
Stack Operations
The stack retention is a LIFO (last-in first-out) retentivity, which describes the way that data are stored and removed from the stack.

Hexadecimal to Decimal converter
Hex to Binary converter
Hex Calculator
IEEE-754 Floating Betoken Converter
x86 Registers
Source: https://vinesmsuic.github.io/2020/02/20/notes-csp/
Posted by: martinezglaimfor.blogspot.com


0 Response to "What Are Program Invisible Registers"
Post a Comment